Protecting Your Pathology: Cybersecurity for Digital Workflows
Digital pathology opens up new cybersecurity risks for labs—but simple steps can mitigate those risks and increase digital resilience

For many labs, digital technologies have been a game changer. Tedious tasks can be automated, remote consultations are faster and easier, broken slides are a thing of the past—even the ergonomics are improved. But digital pathology has one weakness glass slides lack: a vulnerability to cyberattacks. How vulnerable are today’s labs to such intrusions—and what can they do to mitigate the risks?
Vulnerabilities in the lab
“I’m sure many of us have seen news items about data breaches at major hospital networks,” says Naveen Chandra, vice president and general manager for digital pathology at Leica Biosystems. “This is driving a surge of interest in cybersecurity from the healthcare community. That being said, the level of attention and resources dedicated to these issues varies by institution.”

Risks involved in digital pathology and other forms of image information exchange include malware on storage media or embedded directly in images or reports, bad actors infiltrating lab or hospital networks or manipulating HL7 messages, attacks against artificial intelligence (AI) tools used for diagnosis or lab operations, or even malicious editing of the images themselves. Studies have also found that, although security measures exist to protect against these kinds of attacks, many labs and hospitals fail to implement them.1
But some of the lab’s most significant cybersecurity risks come not from software or equipment, but from operators. “From our observations, credential phishing is one of today’s greatest cybersecurity threats,” says Chandra. “This occurs when threat actors take advantage of unsuspecting victims through social engineering tactics. Compromised credentials can lead to ransomware attacks with devastating outcomes like the ones we’ve seen in the news.”
Combating threats
Well over half of all cyberattacks against healthcare institutions arise from general email phishing, with several other forms of phishing close behind (see Figure 1).2
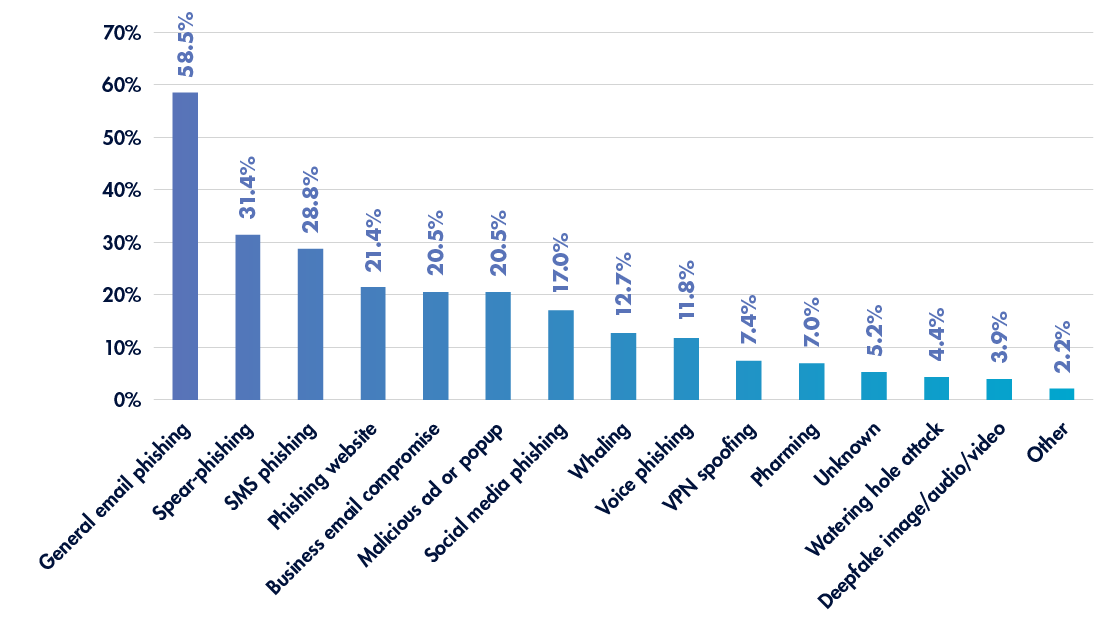
Training staff to spot and avoid social engineering tactics—for instance, by using URL expanders to examine unfamiliar links, verifying the origins of unusual messages, and reporting suspicious emails—can go a long way toward protecting labs against cyberattacks initiated by phishing. “Cybersecurity awareness training is the primary tool used to combat this threat—and we use it within our organization, too,” says Chandra, who emphasizes that increasing labs’ digital security can be an accessible and affordable process.
“There are always opportunities to increase security, and many of them can be through cost-conscious methods—you do not have to ‘break the bank’ just to be secure,” he says. “Three easy, low-investment programs that yield powerful outcomes in a multi-pronged cybersecurity defense stance include enforcement of 1) need to know, 2) principle of least privilege, and 3) routine employee access reviews. These initiatives, which have a lot of educational material readily available, can greatly limit the blast radius of a cybersecurity attack if compromised employee credentials are exploited.”
| Simple cybersecurity defenses | |
| Need to know | The need-to-know principle involves restricting access to potentially sensitive information, giving personnel only the access they need to complete their duties. |
| Principle of least privilege | This principle restricts what people and applications can do with information and digital assets, ensuring that they only have the capabilities necessary for their work. |
| Employee access reviews | Labs should regularly ensure that they are adhering to principles of need-to-know and least privilege, adjusting employees’ access and capabilities based on their work and verifying that any unnecessary privileges or departed employees are removed. |
Emerging cybersecurity concerns
Digital technologies are rapidly advancing in the lab—and cybersecurity considerations are changing equally fast. As an example, Chandra highlights recent revisions3—and further proposed updates4—to the FDA’s cybersecurity requirements for premarket submissions. “Digital pathology and telepathology devices must incorporate a range of safeguards to protect patients’ privacy and laboratories’ data through technical measures, process standardization, and best practices aligned with regulatory requirements,” he explains. “As a manufacturer, from a technical control perspective, we bake measures like firewalls and application whitelisting into the architecture of our products. We also include robust instructions for use that recommend best practices to fortify the laboratory’s security posture to complement the installation of the product.”
The more connected laboratories become, the more potential weaknesses may be introduced into the system. “With the widespread adoption of cloud computing, remote access of digital resources ushers in ease of use, but also broadens an organization’s attack surface for threat actors,” says Chandra. “Zero trust is a framework that can make a significant improvement in an organization’s cybersecurity program.5 This framework requires all users—whether inside the organization’s network or remote—to be authenticated and, most importantly, authorized before they are granted access to computer resources.” A zero trust model can be extended to not just providers, but also patients, payers, administrators, and even instruments that are networked into the lab’s systems, closing information security gaps and mitigating insider threats.6
As more laboratories transition to digital workflows and automated technologies, cybersecurity will become increasingly complex—and, with every new technology that takes its place in the lab, threat actors will seek opportunities to exploit it. This is especially true in areas like digital and computational pathology, where security vulnerabilities remain7 and technologies are advancing faster than the infrastructure and standards8 that accompany them.
“The rapid embrace of AI will make cyberattacks more sophisticated, so we as an industry must leverage internal and external knowledge sharing opportunities to keep abreast of new trends,” warns Chandra. “The cybersecurity landscape is continually evolving and we must all prioritize cybersecurity in our current products and in the development of future products.”
Top takeaways for labs
- Consider your lab’s expertise. Where are the gaps in training and what resources are available to alleviate those gaps? You may be able to partner with your institution’s IT department for additional training; alternatively, governments, professional associations, and private consulting firms may have educational offerings available.
- Evaluate your cybersecurity efforts. Are there opportunities to increase security without sacrificing practicality? If you don’t already follow the principles of need-to-know and least privilege, these are a simple starting point for labs new to managing cybersecurity issues.
- Build collaborations. Know your IT, security, and informatics professionals. You never know when you’ll encounter a tricky question, a suspicious file, or—despite your best efforts—a cybersecurity emergency. Understanding when to defer to the experts and being able to reach the right person at the right time can go a long way to mitigating risk and minimizing the impact of potential issues.
References:
- Eichelberg M et al. Cybersecurity challenges for PACS and medical imaging. Acad Radiol. 2020;27(8):1126–1139. doi:10.1016/j.acra.2020.03.026.
- Healthcare Information and Management Systems Society. 2023 HIMMS Healthcare Cybersecurity Survey. March 1, 2024. https://www.himss.org/sites/hde/files/media/file/2024/03/01/2023-himss-cybersecurity-survey-x.pdf.
- U.S. Food and Drug Administration. Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions. September 27, 2023. https://www.fda.gov/media/119933/download.
- Select Updates for the Premarket Cybersecurity Guidance: Section 524B of the Federal Food, Drug, and Cosmetic Act; Draft Guidance for Industry and Food and Drug Administration Staff; Availability. Federal Register. March 13, 2024. https://www.govinfo.gov/content/pkg/FR-2024-03-13/pdf/2024-05295.pdf.
- Goldstein E. No Trust? No Problem: Maturing Towards Zero Trust Architectures. Cybersecurity & Infrastructure Security Agency. September 7, 2021. https://www.cisa.gov/news-events/news/no-trust-no-problem-maturing-towards-zero-trust-architectures.
- Edo OC et al. A zero trust architecture for health information systems. Health Technol. 2024;14:189–199. doi:10.1007/s12553-023-00809-4.
- Holub P et al. Privacy risks of whole-slide image sharing in digital pathology. Nat Commun. 2023;14(1):2577. doi:10.1038/s41467-023-37991-y.
- Abels E et al. Computational pathology definitions, best practices, and recommendations for regulatory guidance: a white paper from the Digital Pathology Association. J Pathol. 2019;249(3):286–294. doi:10.1002/path.5331.
Subscribe to Clinical Diagnostics Insider to view
Start a Free Trial for immediate access to this article